-
Notifications
You must be signed in to change notification settings - Fork 50
Updates trypurescript to work with Halogen Affjax example #203
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Conversation
Currently, the affjax example in Halogen does not work and returns the following response: ``` Blocked form submission to '' because the form's frame is sandboxed and the 'allow-forms' permission is not set. ``` I believe this fixes the issue, although I haven't tested it yet. Thanks!
|
Here's the example for reference: From this section: |
|
Thanks for the PR. I’d like to do a bit of research about the security implications of allowing forms here before accepting. (I assume that allow-forms is disabled by default for a reason). |
|
@hdgarrood as far as I understand it, the risk of allowing forms via an iframe is that the form submission can POST some data off to a server when you may not have wanted that. Yet due to For example, in the linked Halogen example if you use the click event instead of the submission event then the request goes through perfectly fine. So I'm not sure what we gain by blocking form submission within this iframe. |
|
Does the form submission let you navigate away from the host page within the frame? |
|
I believe that to do that you would have the form trigger a JS handler which changes the iframe location. But I also think that's already possible to do via Resources are blocked by the same-origin policy, but navigation seems possible. |
|
It's not clear to me your dev console is executing within the context (security policy) of the inner iframe. I don't think testing it in the dev console is a robust way of verifying the security of it. |
|
I agree that the dev console isn't the proper way to check this. That said, the console is executing within the JS context of the iframe: Though perhaps that doesn't necessarily mean it's subject to the iframe's security policy. It seems that it is, but I'm open to suggestions for better ways to check this. |
|
I would verify it with DOM APIs in PureScript code if available. If the APIs are unavailable, you can hack around it with |
|
The APIs are unavailable (from a quick glance through Pursuit), so I can hack around it later today. |
|
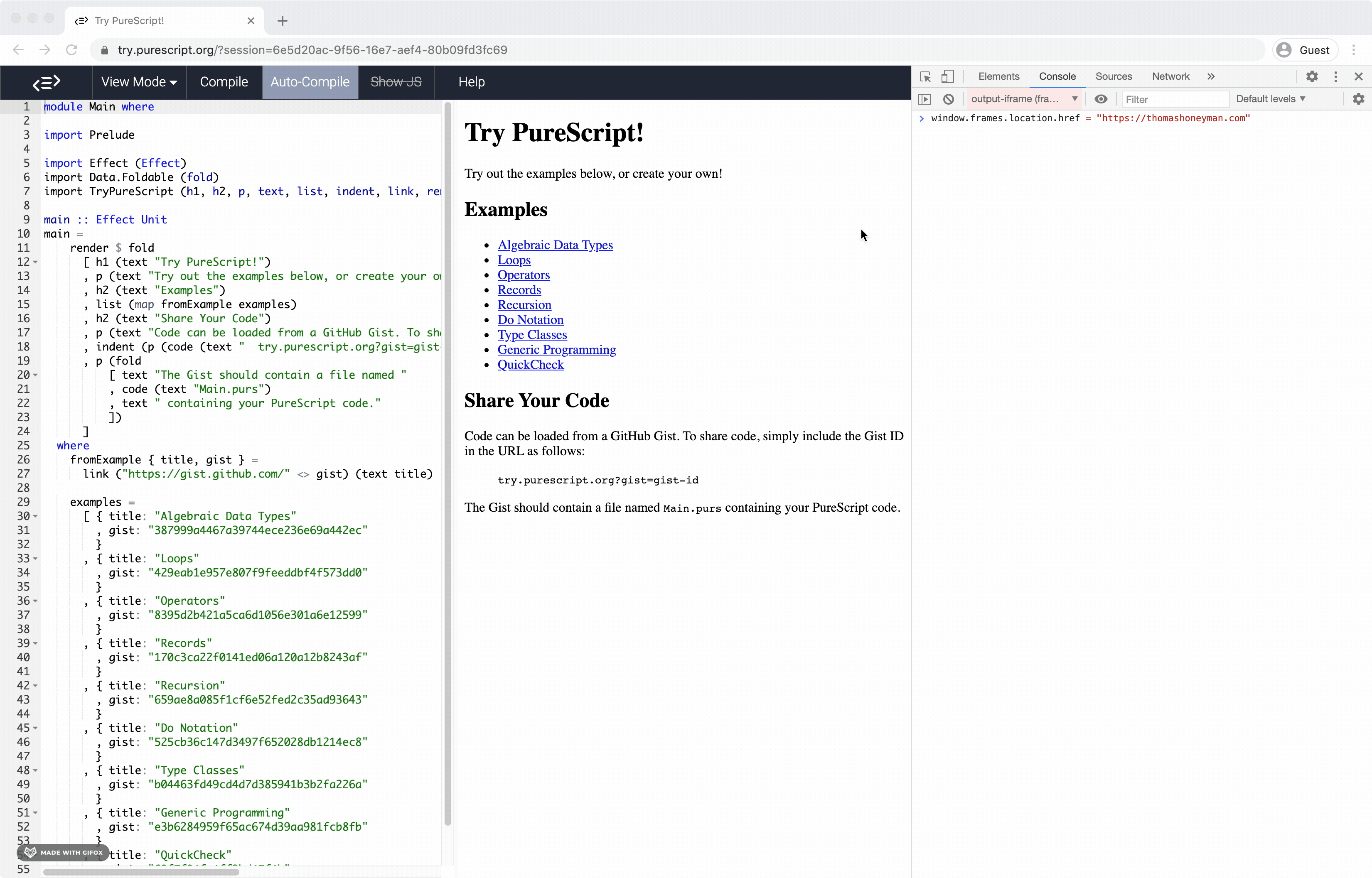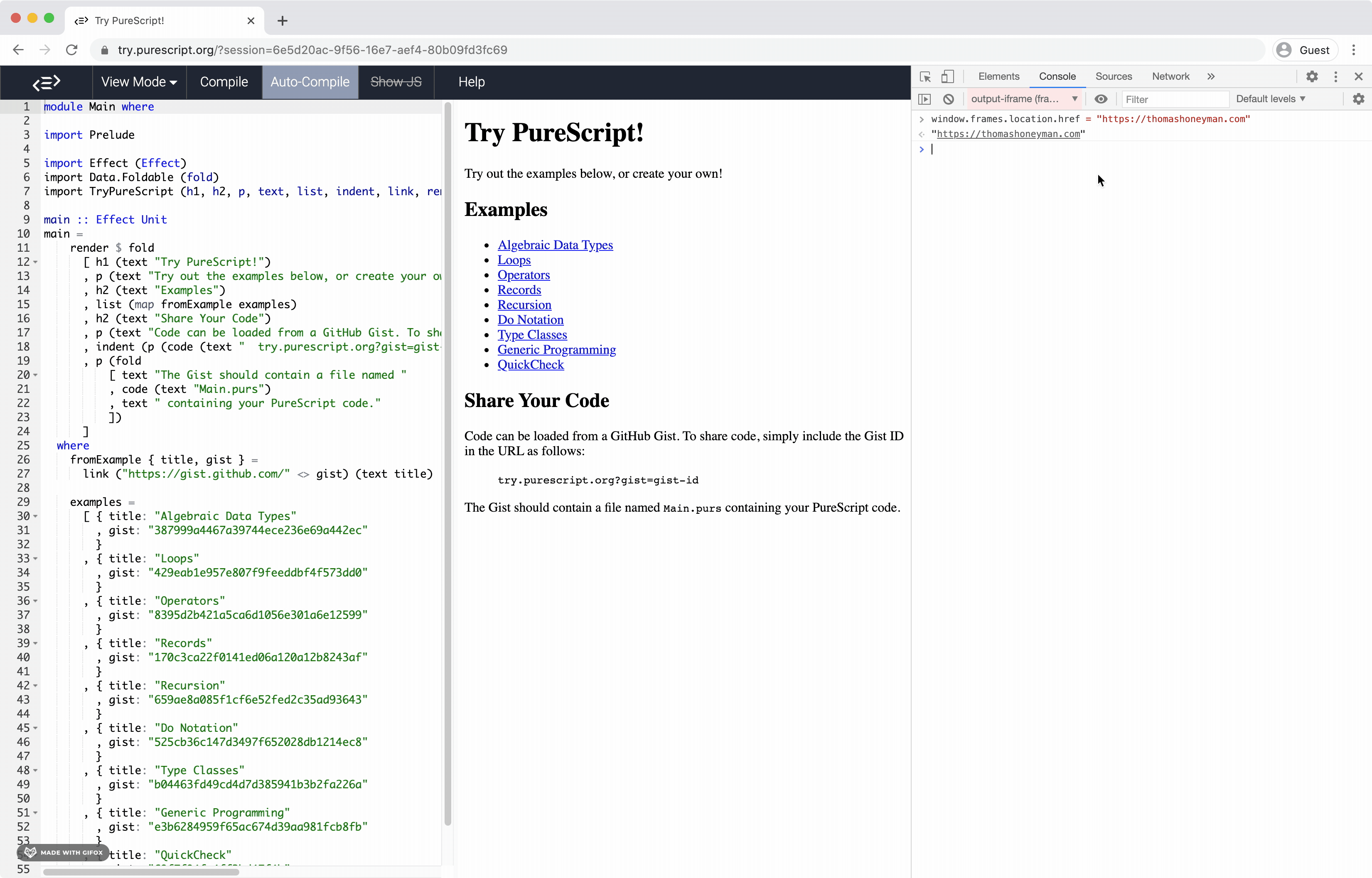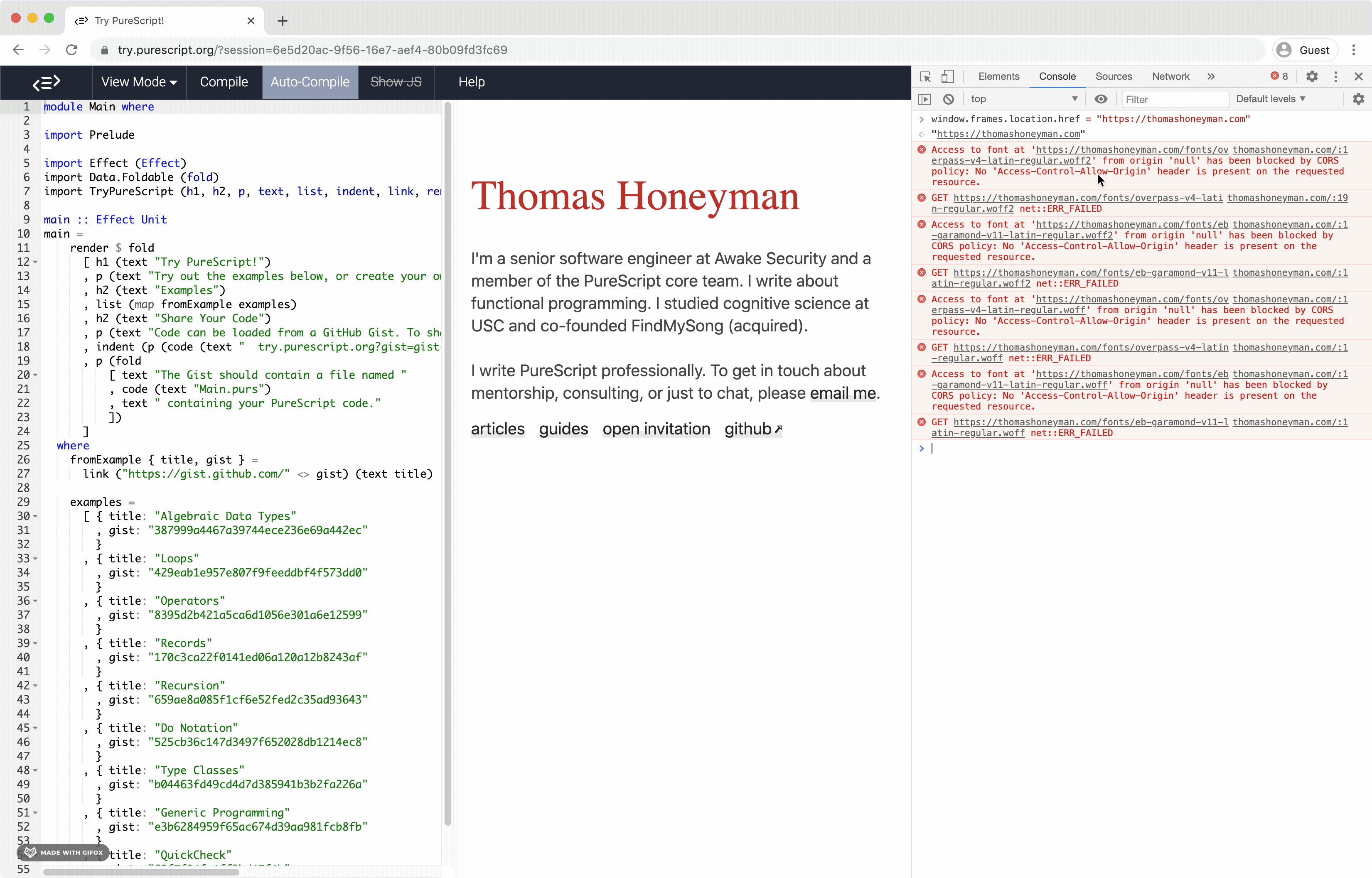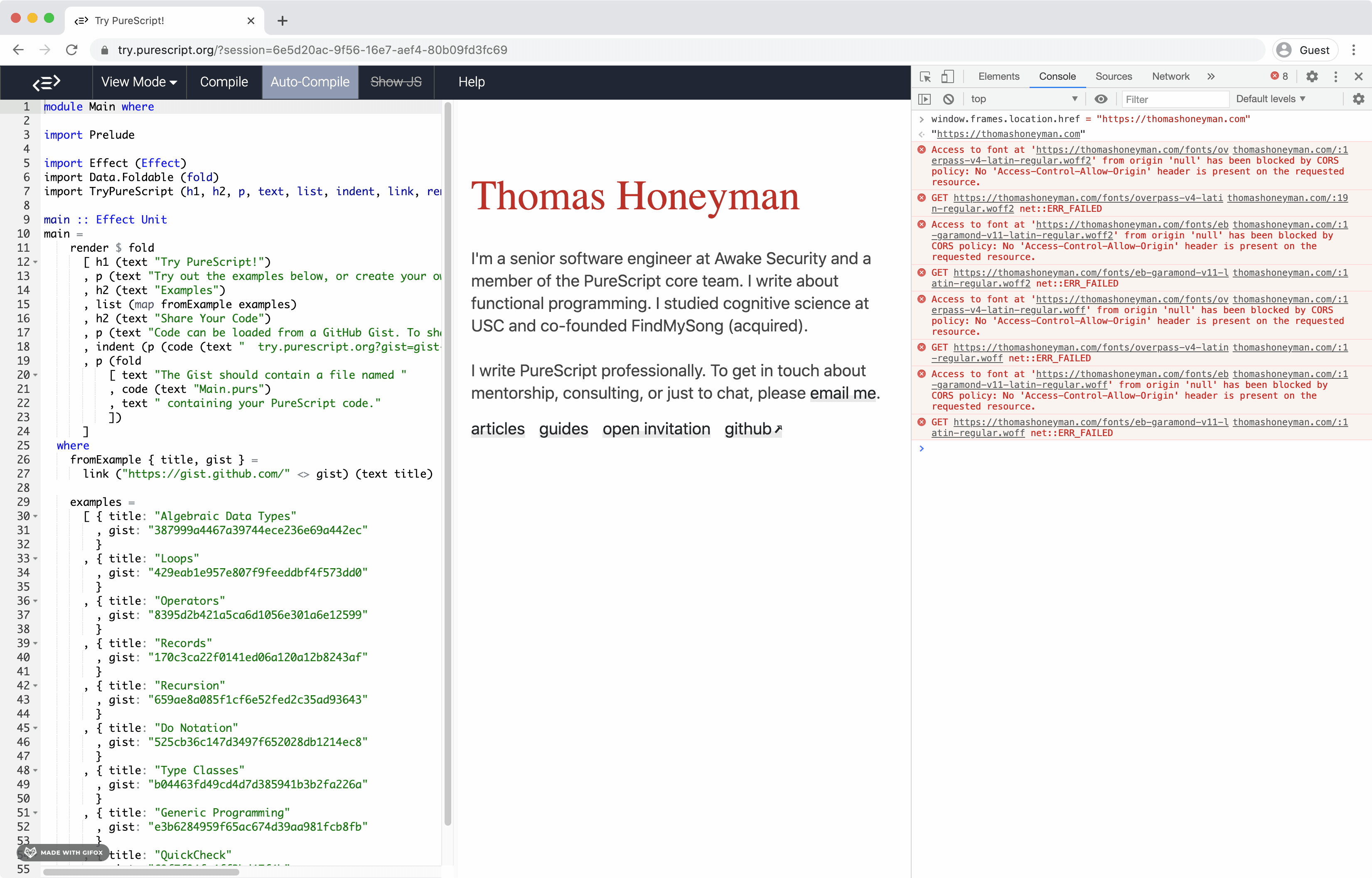
I was able to use module Main where
import Prelude
import Effect (Effect)
import Web.HTML (window)
import Web.HTML.Location (setHref)
import TryPureScript
import Debug.Trace
import Unsafe.Coerce (unsafeCoerce)
main :: Effect Unit
main = do
win <- window
let loc = (unsafeCoerce win).frames.location
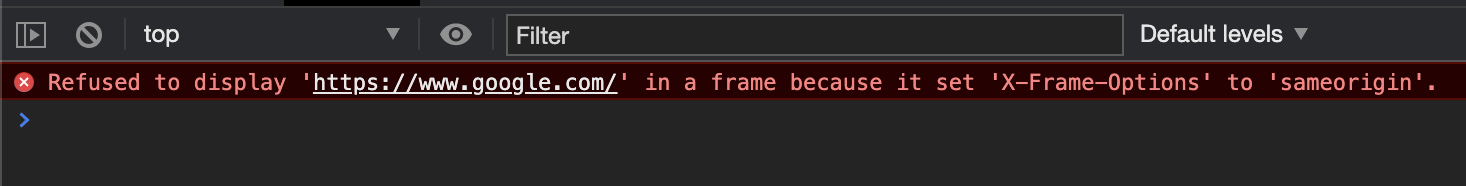
setHref "https://google.com" loc
pure unitand it was blocked |
|
So as long as a form submission does the same thing I'm ok with allowing it. |
|
Oh whoops! that's due to a header on google.com specifically. You are correct, unfortunately allow-scripts does let you change the location within the iframe. I'm inclined to agree with you then. |
|
Fortunately it doesn't navigate the top-level window and the iframe is still sandboxed. |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Given the discussion we've had so far, I think that adding this functionality doesn't increase our security risk and unblocks a nice use case for Try PureScript.
Currently, the affjax example in Halogen does not work and returns the following response:
I believe this fixes the issue, although I haven't tested it yet. Thanks!